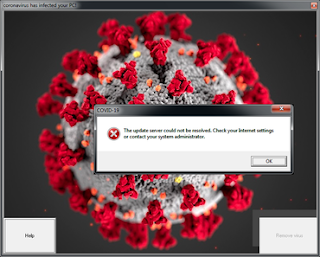
There is now COVID-19 malware Which will wipe your PC and rewrite your MBR
Together with the coronavirus (COVID-19) pandemic raging throughout the world, some malware writers have developed malware which destroys...
https://tech-blog24.blogspot.com/2020/04/there-is-now-covid-19-malware-which.html
Together with the coronavirus (COVID-19) pandemic raging throughout the world, some malware writers have developed malware which destroys infected programs, by simply wiping files or restarting a pc's master boot record (MBR).
With assistance from the infosec community, ZDNet has recognized at least five malware breeds, some dispersed in the wild, but some seem to have been produced just as evaluations or jokes.
The frequent theme among all four trials is they utilize a coronavirus-theme and they are geared towards destruction, instead of monetary gain.
One of the four malware trials utilized by security researchers last month, the most innovative were the 2 samples which rewrote MBR businesses.
Some innovative technical understanding was required to make such breeds as tinkering with a master boot record is not an easy effort and may easily lead to systems which didn't boot in any way.
The very first of this MBR-rewriters has been found with a security researcher which goes by the title of MalwareHunterTeam, also in depth at a report by SonicWall this past week. Utilizing the title of COVID-19.exe, this malware infects a computer and contains two disease phases.
At the first stage, it merely reveals an annoying window which users can not shut as the malware also has disabled the Windows Task Manager.
IT privacy and security: Concerns, initiatives, and forecasts (TechRepublic Premium)
For all the most recent research reports, 100+ ready policies, IT job descriptions, and much more, check out TechRepubli...
While users try to manage this window, the malware is quietly rewriting the computer master boot record supporting their back. It then restarts the PC, as well as also the new MBR kicks in, blocking users to some pre-boot display.
Users may finally regain access to their own computers, but they will need exceptional programs which may be employed to recover and reconstruct the MBR into a working condition.
However there was a 2nd coronavirus-themed malware breed that re-wrote that the MBR. This is a far more convoluted malware surgery.
It introduced as the"CoronaVirus ransomware" however, it was just a facade. The malware main purpose was to steal passwords from an infected host then mimic ransomware to deceive the consumer and conceal its real intent.
But, it was not ransomware either. It just posed as you can. With users viewing ransom notes and not having the ability to get their PCs, the final thing users will thing to do would be to check if a person exfiltrated passwords out of their programs.
Based on investigation from SentinelOne safety researcher Vitali Kremez and Bleeping Computer, the malware additionally included code to wipe files onto the user's systems, however this did not seem to be active at the variant they examined.
In addition, this one was spotted twice, using another variant found by G DATA malware writer Karsten Hahn, fourteen days later. This time, the malware maintained the MBR-rewriting capacities but replaced the information wiping attribute using a practical screen-locker.
But security researchers have seen over coronavirus-themed MBR-rewriters. They also seen two information wipers.
Both were uncovered by MalwareHunterTeam.
The very first was seen back in February. It utilized a Chinese record name, and most probably targeted Chinese consumers, though we do not have advice if it had been dispersed in the wild or has been a test.
The next was seen yesterday, and this one was discovered uploaded to the VirusTotal portal site by somebody located in Italy.
MalwareHunterTeam explained both breeds as"bad wipers" due to the ineffective, error-prone, and time-consuming procedures that they used to divert files on infected systems. But they functioned, which made them unsafe should spread in the wild.
It may look odd that some malware writers create harmful malware in this way, but it is not the first time this occurred. For every single financially-motivated malware breed which security researchers find, there is also one which has been made as a joke, only for the giggles. Something similar occurred during the WannaCry ransomware outbreak in 2017, when days following the first WannaCry ransomware encrypted servers all around the planet, there were innumerable of clones doing exactly the identical thing for no clear reason.
With assistance from the infosec community, ZDNet has recognized at least five malware breeds, some dispersed in the wild, but some seem to have been produced just as evaluations or jokes.
The frequent theme among all four trials is they utilize a coronavirus-theme and they are geared towards destruction, instead of monetary gain.
One of the four malware trials utilized by security researchers last month, the most innovative were the 2 samples which rewrote MBR businesses.
Some innovative technical understanding was required to make such breeds as tinkering with a master boot record is not an easy effort and may easily lead to systems which didn't boot in any way.
The very first of this MBR-rewriters has been found with a security researcher which goes by the title of MalwareHunterTeam, also in depth at a report by SonicWall this past week. Utilizing the title of COVID-19.exe, this malware infects a computer and contains two disease phases.
At the first stage, it merely reveals an annoying window which users can not shut as the malware also has disabled the Windows Task Manager.
IT privacy and security: Concerns, initiatives, and forecasts (TechRepublic Premium)
For all the most recent research reports, 100+ ready policies, IT job descriptions, and much more, check out TechRepubli...
While users try to manage this window, the malware is quietly rewriting the computer master boot record supporting their back. It then restarts the PC, as well as also the new MBR kicks in, blocking users to some pre-boot display.
Users may finally regain access to their own computers, but they will need exceptional programs which may be employed to recover and reconstruct the MBR into a working condition.
However there was a 2nd coronavirus-themed malware breed that re-wrote that the MBR. This is a far more convoluted malware surgery.
It introduced as the"CoronaVirus ransomware" however, it was just a facade. The malware main purpose was to steal passwords from an infected host then mimic ransomware to deceive the consumer and conceal its real intent.
But, it was not ransomware either. It just posed as you can. With users viewing ransom notes and not having the ability to get their PCs, the final thing users will thing to do would be to check if a person exfiltrated passwords out of their programs.
Based on investigation from SentinelOne safety researcher Vitali Kremez and Bleeping Computer, the malware additionally included code to wipe files onto the user's systems, however this did not seem to be active at the variant they examined.
In addition, this one was spotted twice, using another variant found by G DATA malware writer Karsten Hahn, fourteen days later. This time, the malware maintained the MBR-rewriting capacities but replaced the information wiping attribute using a practical screen-locker.
But security researchers have seen over coronavirus-themed MBR-rewriters. They also seen two information wipers.
Both were uncovered by MalwareHunterTeam.
The very first was seen back in February. It utilized a Chinese record name, and most probably targeted Chinese consumers, though we do not have advice if it had been dispersed in the wild or has been a test.
The next was seen yesterday, and this one was discovered uploaded to the VirusTotal portal site by somebody located in Italy.
MalwareHunterTeam explained both breeds as"bad wipers" due to the ineffective, error-prone, and time-consuming procedures that they used to divert files on infected systems. But they functioned, which made them unsafe should spread in the wild.
It may look odd that some malware writers create harmful malware in this way, but it is not the first time this occurred. For every single financially-motivated malware breed which security researchers find, there is also one which has been made as a joke, only for the giggles. Something similar occurred during the WannaCry ransomware outbreak in 2017, when days following the first WannaCry ransomware encrypted servers all around the planet, there were innumerable of clones doing exactly the identical thing for no clear reason.